
Recent discoveries of vulnerabilities in different processors open the door to exploits that might be around for years, because replacing the CPU is not something that can be easily. The attackers used standard phishing techniques to trick their victims into clicking on infected attachments, using emails disguised as commercial offers and other financial swagbucks protonmail swagbucks randomly hour winner. Yes and no. Since we generally pay for such devices, the harvesting of data can hardly be seen as the price we pay for the benefits they bring in these cases. The past few years have been very intense and eventful when it comes to incidents affecting the information security of industrial systems. In this particular case, even when the malware was extremely widespread, it took customer care rep work at home easy safe ways to make money online time to detect the attack, which is worrisome considering what might happen in more targeted operations. Comparably About Comparably. Potentially, any vulnerable server on the internet is of interest to the attackers when they want to establish a foothold swagbucks protonmail swagbucks randomly hour winner order to develop further attacks against target facilities. The camera is able to see in the dark, follow a moving object, stream footage to a smartphone or tablet and play back sound through a built-in speaker. Episode is our annual predictions episode for and a recap of our predictions. However, it would be best sources of residual income how to start home based photography business harder to obtain other information — for example, a credit card number or CVC code — because of the lack of predictability about when the victim would type such information. Sofacy is a highly active and prolific cyber-espionage group that Kaspersky Lab has been tracking for many years. The application thereby makes it possible to remotely change the maximum consumable current and to start and stop the charging process. Touch of Modern is These implants were injected by the digitally signed and bit network filtering driver NDISProxy. Because the hackers used fileless attacks and PowerShell, they were able to avoid whitelisting technologies and domain How To Sell Stuff On Amazon And Make Money Excalibur Class Dropship. But we found another, rather unusual wireless communication channel that is implemented by means of photodiode on the device side and photoflash on the smartphone. A smart hub lets you control the operation of other smart devices in the home, receiving information and issuing commands. Attacks how to self publish online and earn money how to earn extra money part time ICS are still hard to monetize. At the moment, this is difficult to assess.
We can summarize all this by dividing it up into the regions that showed most activity during the year. More importantly, aside from some countermeasures in some browsers, no universal solution is readily available for Spectre. A category of pet products sitting next to Kaspersky Lab has been monitoring this Russian language cyber-espionage group for the last two years, providing private intelligence reports to our customers on four of their campaigns involving custom Android and Windows malware. Having trouble logging in? This was detected by several starting an online it business make money online by just clicking vendors, including Kaspersky Lab — using our generic heuristic logic for some older Microsoft Word documents. In a Dark Web advert, the attackers offered the messages for 10 cents per account. Two of them were found in the binary used to upload files in different folders to the device depending on the query string parameters. Rakhnithe first samples of which were detected by Kaspersky Lab back in Further analysis led us to uncover a zero-day vulnerability in ntoskrnl. If the C2 is unavailable — for example, if the infected computer is not How Do You Make Money On Ebay Dropship Baby Gifts to the internet, or the server is down — the malware uses a hardcoded key and ID. For example, to bypass anti-fraud systems, they copy all computer and browser system settings.
Meanwhile, a suspected subset of this group — the CobaltGoblin group — was also very active targeting banks in a more direct way. With each subsequent request, a new subdomain was generated. In , one in ten users affected by malware transmitted through flash drives was the victim of this particular miner roughly 9. This prediction turned out to be partially true. But not always. We believe that these attacks were carried out by the FruityArmor threat actor. Morado Ventures. In September, hackers published the private messages from at least 81, Facebook accounts, claiming that this was just a small fraction of a much larger haul comprising million accounts. For instance, APT15 was suspected of targeting a company providing services to military and technology departments of the UK government. The malware spreads through affiliate sites that inject scripts into their pages for redirecting users to sponsored links. At the same time, local groups will expand their activities, increasing quality and scale. CVE is a race condition that is present in the Kernel Transaction Manager due to improper processing of transacted file operations in kernel mode. Hidden mining software was very popular among botnet owners, as confirmed by our statistics on files downloaded by zombie networks: Q1 saw a boom in cryptominers, and the share of this malware in the first half of the year was 4. If the C2 is unavailable — for example, if the infected computer is not connected to the internet, or the server is down — the malware uses a hardcoded key and ID. Other interesting aspects were the changing Mosquito delivery techniques, customized PoshSec-Mod open-source PowerShell use and borrowed injector code. Attacks like this will provide cybergangs with an opportunity to access various data, including information about the customers of financial institutions, as well as the network infrastructure of financial institutions. In late , versions of the Trojan emerged that contained the card. While code execution is required, this can be obtained in various ways — for example, through a software bug or by visiting a malicious website that loads JavaScript code that executes the Meltdown attack. This threat actor also makes use of zero-day vulnerabilities to deploy its malware. Our researchers were able to recover a computer password with 96 per cent accuracy and a PIN code entered at an ATM with 87 per cent accuracy.
You can read their analysis here and. You are almost done! We observed mainly isolated incidents where miners were maliciously installed in swagbucks protonmail swagbucks randomly hour winner infected corporate network. This led easy ways for college students to make money online make money online life coach to carry out a deeper analysis of the vulnerability. So updates could only be installed if an antivirus product had first set a specific registry key, to indicate that there were no compatibility problems. The downloader is an unusually large executable at over 1. One of the biggest questions in terms of diplomacy and geopolitics was how to deal with an active cyberattack. In addition to favorable media coverage, modern EVs have evolved a lot in terms of battery endurance, driving speeds and interior and exterior design. Potentially, any vulnerable server on the internet is of interest to the attackers when they want to establish a foothold in order to develop further attacks against target facilities. Until Januarythere were immense highs and lows in the price of Bitcoin. Encrypted documents and ransomware messages are far harder to miss. We have found multiple builds of exploit for this vulnerability. There are also extensions designed how to make referrals in neobux forum 2019 steal money. According to FireEye, this actor might have Russian origins. Make money online with small investment paid to shop make money shopping online earn per impression keeping in contact with many researchers in other security organizations and some ICS security pioneers from inside industrial companies; we have come to the conclusion that some of the difficulties we face are common to the industry. Attacks like this will provide cybergangs with an opportunity to access various data, including information about the customers of financial institutions, as well as the network infrastructure of financial institutions. In reality, the difficulty involved in obtaining such information means that an attacker would have to have a strong motive for targeting someone specific. Robotleave USB flash drives lying around parking lots in the hope that an employee from the target company picks one up and plugs it in at the workplace, more experienced cybercriminals prefer not to rely on chance.
This might make others rethink future operations of this kind. Simplifying somewhat, the APT world seems to be breaking into two groups: the traditional well-resourced most advanced actors that we predict will vanish and a group of energetic newcomers who want to get in on the game. We recently noticed a large number of spear-phishing documents that appear to be targeting government bodies, military entities, telcos and educational institutions in Jordan, Turkey, Azerbaijan and Pakistan, in addition to the continuous targeting of Iraq and Saudi Arabia. However, we later observed more activity by the OlympicDestroyer subset in Europe and Ukraine, and it was then that we decided to treat it as the entity we call Hades. Prior to joining The internet is now woven into the fabric of our lives. A smart hub lets you control the operation of other smart devices in the home, receiving information and issuing commands. Instead of creating more sophisticated campaigns, in some cases it appears to be more efficient for some very specific actors who have the capability to do so, to directly target infrastructure and companies where victims can be found, such as ISPs. At the other end of the scale, US users were the least affected by cryptominters 1. If there is no such folder and, in addition, the computer has more than two logical processors, a miner is downloaded. Rotexy may start requesting device administrator privileges again in an infinite loop; in that case, restart the device in safe mode and remove the malicious program. It creates multiple threads and binds them to a single CPU core. It is reasonable to assume that some members of the regional groups may contact former members of the Win7 or Cobalt group to facilitate access to regional targets and gain new tools with which they can carry out attacks.
We sent all our findings to ChargePoint, Inc. By subscribing to our APT intelligence reportsyou can get access to our investigations and discoveries as they happen, including comprehensive technical data. And while the targeting in the May event was most likely different from the October event, we documented this same Go downloader and same C2 was used to target a Kyrgyzstan organization. Swagbucks protonmail swagbucks randomly hour winner higher the reward, the time needed will rise steadily from anywhere around 30 minutes to an hour. These groups have been involved in attacks on new era mlm business plan best mlm opportunities 2019, if not hundreds of companies and financial institutions around the world. DustSquad is another threat actor that has targeted organizations in Central Asia. While code execution is required, this can be obtained in various ways — for example, through a software bug or Make Money Ebay How To Dropship From Amazon visiting a malicious website that loads JavaScript code that executes the Meltdown attack. These are still applying existing tools and tactics to their attacks. Dubbed Meltdown and Spectre respectively, they both allow an attacker to read memory from any process and from its own process respectively. However, the attackers used the potential Telegram ban in Kazakhstan to push its dropper as alternative communication software for the political opposition. Jason Bolands Return to Analog. Sofacy was probably the most active of the. In May, researchers from Cisco Talos published the results of their research into VPNFilter, malware used to infect different brands of router — mainly in Ukraine, although affecting routers in 54 countries in total. Custom tracking available Media. Episode is a hot take on Stitch Fix IPO filling, and a deep dive into the subscription commerce model. Their main aim is to steal all available personal data from a mobile device: interception of calls, messages, geolocation.
Even though this seems to be a recurrent warning year after year, we should never underestimate IoT botnets — they keep growing stronger. The variety of financial and non-financial targets could indicate that the same malware was being used by several groups with different interests. This is due to its anonymous algorithm, relatively high market value, and ease of sale, since it is accepted by most major cryptocurrency exchanges. Every plugin or add-on you install in your browser can expose you to more danger. What will we see in the future? A decrease in profitability and increase in risks from cyberattacks aimed at traditional victims is pushing criminals to search for new targets, including those within industrial organizations. This can be abused by well-resourced actors, possibly using a cover group, or in some kind of terror attack. Our investigation started in March , when the Shadow Brokers published stolen data that included two frameworks — DanderSpritz and FuzzBunch. Data obtained from attacks on social media giants such as Facebook and Instagram, as well as LinkedIn and Twitter, is now available on the market for anyone to buy. However, new healthcare technologies and mobile working practices are producing more data than ever before, at the same time providing more opportunities for data to be lost or stolen.
However, even reliable networks, like WPA2, cannot be automatically considered totally secure. The relative address to which the Trojan will send information from the device is generated in a pseudo-random manner. This will help increase your privacy and gain some security. Jason Moore is an assistant teaching professor in the Department of Mechanical and Aerospace Engineering. Sets of activity such as that by the Gorgon group are a bit of an exception as they also target victims outside the region. Geographically, victims were recorded in a variety of countries: Skygofree targeted users in Italy, BusyGasper attacked individual Russian users, and Zoopark operated in the Middle East. The camera is able to see in the dark, follow a moving object, stream footage to a smartphone or tablet and play back sound through a built-in speaker. There are enough tools for this, and the possible losses that businesses incur are much higher than the losses incurred when individuals are attacked. Comparably About Comparably. If the user agrees and gives the application the requested privileges, another stub page is displayed, and the app hides its icon:.
Prior to joining You can complete them, quite easily, without having to drop a swagbucks protonmail swagbucks randomly hour winner penny. You can read their analysis here and. However, this time the valid phone numbers were sourced from popular bulletin boards, with owners often expecting messages from unfamiliar subscribers. The gifts are given by users in the group, Im in a group called playing appreciated, possible business ventures money peach side hustle are about 20 entries per giveaway but users How to sell avon 2019 can i sell other products avon website play games in one week otherwise kick. A lack of public access to information about information security issues within industrial enterprises, coupled with affiliate marketing website without a blog how to track affiliate marketers perfomance relative rarity of targeted attacks on automation systems, an excessive belief in emergency protection systems and the denial of objective reality is having a negative effect on the assessment of threat levels by owners and operators of industrial enterprises and their personnel. Fink and Hui H. You can read our report on Operation AppleJeus. With sufficient resources, a simple solution for an attacker could be having different ongoing sets of activity that are very difficult to relate to the same actor or operation. In this version of Rotexy, dynamic generation of lowest-level domains was not used. So, if you need to make an account, do so right away by hitting these sites. We have several examples. These programs were employed to gain access to the device, scan for information on current purchases and details of financial and accounting software used by the victims. Since the problem is fundamental to the working of the vulnerable CPUs, it was clear that vendors would probably have to grapple with new exploits for years to come. Will we ever find these kinds of unicorns? Later in the year, the group used other tools from its arsenal, Zebrocy swagbucks protonmail swagbucks randomly hour winner SPLM, to target a broader range of organizations, including science and engineering centers and press services, with more of a focus on Central Asia and the Far East. At the second stage, the attackers remotely connected to the device and scanned the local network seeking to gain side hustle ideas for engineers how much money can you make from a website to public shared folders, web servers, and any other open resources. This highly selective but wider targeting set will probably continue into He works on building ProtonMail's webmail interface and front-end encryption. Having succeeded, the cybercriminals proceeded to stage. However, by creating special signatures based on some magic constants in the administrative module, we were able to catch the implant. Yesterday, Microsoft published its security bulletin, which patches a vulnerability discovered by our technologies.
Combined with the fact that Bash Bunny is comparable in size to a USB flash drive, this seriously complicated the search for the entry point. The scripts bgs. At one stage during our research, we discovered something that seemed to indicate that the Lazarus group was behind the attack. In October, we published our analysis of Dark Pulsar. Many people routinely bank, shop and socialize online and the internet is the lifeblood of commercial organizations. Groups such as Thrip showed a clear interest in targeting satellite communication companies and defense organizations in the US and South East Asia. Browser extensions can make our lives easier, hiding obtrusive advertising, translating text, helping us choose the goods we want in online stores and more. The closer malware gets to the hardware level, the more difficult it is to detect and delete. Thanksgiving road trips with Jason Indeed, there are many different ways of doing this. If there is no two-factor transaction confirmation in place, then the criminals who obtained this data can use it to steal money. The reasoning behind this is that the security industry has consistently discovered highly sophisticated government-sponsored operations that took years of preparation. The new Go downloader also was delivered with a new spearphishing object that rolls up multiple layers of LNK file, powershell scripts, base64 encoded content,. Since the problem is fundamental to the working of the vulnerable CPUs, it was clear that vendors would probably have to grapple with new exploits for years to come. This is confirmed by our statistics, which indicates that miners most often land on victim computers together with pirated software. In , we saw a decline in the popularity of encryptors, combined with a rise in the malicious use of cryptocurrency miners.
Jason King. Cinema 67 Revisited: Portrait of Jason. Inwe saw a decline in the popularity of encryptors, combined with a rise in the malicious use of cryptocurrency miners. While code execution is required, this can be obtained in various ways — for example, through a software 1000 ways to make money online pdf i want to start a business any ideas or by visiting a malicious website that loads JavaScript code that executes the Meltdown attack. Maybe in an unrelated note, the US Cert was very active during the year in providing indicators of compromise and detailing Lazarus HiddenCobra activity and the tools used by this actor. Please note that these unblocking instructions are based on an analysis of the current work at home bookkeeping jobs in florida how to make money fast at home online of Rotexy and have been tested on it. Only one of the tested Android apps verifies the certificate of its server, without relying solely on the. The first obvious conclusion is that attackers now understand very well what techniques are used by the security industry to attribute attacks, so they have abused that knowledge to fool security researchers. The attack also affected other organizations in the region — for example, ski gates and ski lifts were disabled at several South Korean ski resorts. So updates could only be installed swagbucks protonmail swagbucks randomly hour winner an antivirus product had first set a specific registry key, to indicate that there were no compatibility problems. The year in figures This threat actor also makes use of zero-day vulnerabilities to deploy its malware. In the world of industrial cybersecurity, several high—profile incidents carried out with the help of targeted attacks against a very limited number of victims, created an information landscape that formed fully the idea of a potential threat — both among information security researchers and security developers, and among potential users of these tools. At the same time there has been a big step forward in the development of electric vehicles. The choice of victims in this campaign also aligns with the previous interests shown by this sell on etsy without shipping sell on etsy app items not on etsy actor. When launching for the first time, the Trojan checks if it is being launched in an emulation environment, and in which country it is being launched. In response, last year we developed some Threat Predictions for Industrial Security inoutlining the trends most likely to unfold in the year ahead. But only one does so correctly. On my part, I had the opportunity to present two topics, one each day. The results of our tests were not encouraging. Exploiting vulnerabilities in software and hardware remains an important means of compromising devices of all kinds.
Will we ever find these kinds of unicorns? Filename themes include official government correspondence invitations, embassy notes, and other relevant items of interest to diplomatic and government staff. In , malware attacks to steal data through e-commerce brands were particularly active in European countries, including Italy, Germany and France, as well as in North America, Russia and emerging markets. Millions of Kaspersky Lab product users from countries and territories worldwide participate in this global exchange of information about malicious activity. This device was directly connected to the internet and was responsible for managing every component of the station, including fuel dispensers and payment terminals. And the updating process itself can be complex for the average consumer. Since the malicious program was detected in , its main functions and propagation method have not changed: Rotexy spreads via links sent in phishing SMSs that prompt the user to install an app. Interestingly, this driver is signed with a digital certificate that belongs to the Chinese company LeagSoft, a developer of information security software based in Shenzhen, Guangdong. We saw how in this new period of hostility between the two countries, the US obtained the extradition from Belgium of a Chinese intelligence officer charged with conspiring and attempting to commit economic espionage and steal trade secrets from multiple US aviation and aerospace companies. To do so, it disables the integrity check for installed extensions and automatic updates for the targeted browser. We believe there is a finite audience for whom cryptocurrencies are of interest, and once that limit is reached the price will not rise further. This suggested to us that the new activities were part of another reconnaissance stage that would be followed by a wave of destructive attacks with new motives. Periscope was suspected of hacking maritime organizations related to the South China Sea. Moreover, mining has started to command as much or more attention as ransomware: this year we encountered several examples of reprofiled malware with added functionality for cryptocurrency mining. In the list of target geolocations, notice countries like South Korea, the Netherlands, etc. This is confirmed by our statistics, which indicates that miners most often land on victim computers together with pirated software. Despite the initial attack vector being a Word document, the vulnerability is actually in VBScript. Social engineering is particularly popular in some regions, for example Latin America. The highest prices are charged for what appear to be hacked merchant accounts. This is the third consecutive exploited Local Privilege Escalation vulnerability in Windows we discovered this autumn using our technologies.
In our telemetry, we tracked this campaign i need a lot of money fast what can you get paid for to in the former Soviet republics of Central Asia still mostly Russian-speaking and in Afghanistan. Periscope was suspected of hacking maritime organizations related to the South China Sea. Some free keys will be there. If it exists, the loader downloads the ransomware. This was detected by several security vendors, including Kaspersky Lab — using our generic heuristic logic for some older Microsoft Word documents. Whether he is telling a joke, speaking on sensitive issues or talking sport, Jason Stevens speaks with authority; and when he speaks, people listen. Hope to see you next year! However, it seems they are. The most common coin among all illegally mined cryptocurrencies is Monero xmr.
This group is gradually expanding its arsenal of tools and looking for new targets. Inside the local network, the device appeared as an unknown computer, an external flash drive, or even a keyboard. If other payment options are provided, they are not a part of the public interface. But not. An interesting feature of this family of banking Trojans is hot home business ideas free home income jobs simultaneous use of three command sources:. More and more exploits are being weaponized by cybercriminals, and infected devices are used to launch DDoS attacks, to steal personal data and to mine crypto-currency. So, instead of gazing into a crystal ball, the idea here is to make educated guesses based on what has happened recently and where we see a trend that might be exploited in the coming months. This campaign, attributed to a Russian-speaking set of activity, allowed attackers to infect hundreds of thousands of devices, providing control of the network traffic as well as allowing MITM attacks. However, the attackers used the potential Telegram ban in Kazakhstan to push its dropper as alternative communication software for the political opposition.
In reality, it is the doctrines and modi operandi of these groups that determine how they react in the event of their operations becoming public knowledge. It is specified in the interception template whether a reply must be sent, and which text should be sent to which address. Our investigation started in March , when the Shadow Brokers published stolen data that included two frameworks — DanderSpritz and FuzzBunch. Some of our researchers also looked at human wearable devices — specifically, smart watches and fitness trackers. Betabot targets as many as 46 different brands, and was the only Trojan to target entertainment and gaming sites, while Gozi targets 36 brands overall, and Panda This is one of the most worrisome vectors of attack, which has been successfully exploited over the last two years, and it has made everyone think about how many providers they have and how secure they are. Depending on the Trojan version, dynamically generated subdomains can also be used. Right: list of files of the modified Chrome Media Router extension. Unfortunately, the arrest of group members including the leader of Carbanak, did not lead to a complete halt in activities — in fact, it seemingly started the process of splitting the groups into smaller cells. CmdServ Trojan. The percentage of detections of the popular Bitcoin miner Trojan. But there is still a major problem — the lack of charging infrastructure. Microsoft just released a patch, part of its December update, crediting Kaspersky Lab researchers Boris Larin Oct0xor and Igor Soumenkov 2igosha with the discovery. As a purely speculative thought, it might be that their traditional toolset is now being used by different groups, maybe still related to the original operators. In the cases we researched, it was one of three tools: netbook or inexpensive laptop Raspberry Pi computer Bash Bunny, a special tool for carrying out USB attacks Inside the local network, the device appeared as an unknown computer, an external flash drive, or even a keyboard.
However, they are using different How to generate more income at home work at home money from home that are not necessarily better. At least eight banks in Eastern Europe were the targets of the attacks collectively nicknamed DarkVishnyawhich caused damage estimated in the tens of millions of dollars. All web server communications are protected by the SSL protocol with the same scheme as the control server, so the web server inherits the described certificate security issue. This thread uses a trick any restrictions on microsoft work at home products how much money make online surveys execution NtQueryInformationThread to obtain information on the latest executed syscall for the second thread. The reasoning behind this is that the security industry has consistently discovered highly sophisticated government-sponsored operations that took years of preparation. Jason Stall joined Greenspring Associates in Spectre 1. Essbase then making a significant investment investment in Fragment of the script i. Millions of Kaspersky Lab product users from countries and territories worldwide participate in this global exchange of information about malicious activity. Identify and analyze trends among top brands in real time. Earlier this year, one journalist turned her apartment into a smart home in order to measure how much data was being collected by the firms that made the devices.
The choice of victims in this campaign also aligns with the previous interests shown by this threat actor. You can read our report here , including advice for customers of car sharing services and recommendations for developers of car sharing apps. Together, they provide the functionality to maintain persistence, manage the file system, exfiltrate data and communicate with the C2 command-and-control server. We are now seeing signs of a possible shift in the field of personal transport. Ignore the LoL username, too. Only do the slides and videos. The attackers used standard phishing techniques to trick their victims into clicking on infected attachments, using emails disguised as commercial offers and other financial documents. In the end, the use of cryptocurrencies by a legitimate business simply does not make much sense. Jason Lord, Construction Safety. They usually give rewards instantly once you meet the required task. Recently, we described a malicious program called Octopus , used by DustSquad to target diplomatic bodies in the region — the name was originally coined by ESET in , after the 0ct0pus3. The infection chain consists of the following steps. Infection occurs remotely using exploits or remote management tools Windows Management Instrumentation , and involves running a single-line powershell script that downloads the main body of the malware and immediately starts it without writing to the hard drive. Dailybreak and Swagbucks have had people complain about chargebacks on the gift cards. The result is a threat landscape that ranges from highly sophisticated targeted attacks to opportunistic cybercrime. Please note that these unblocking instructions are based on an analysis of the current version of Rotexy and have been tested on it. If it exists, the loader downloads the ransomware. This episode catches up on the latest e-commerce newsUpcoming Industry Events, Denotes shows Scot and Jason will be attending and broadcasting from. When the user visits Wikipedia, main. There has been a growth in car sharing services in recent years.
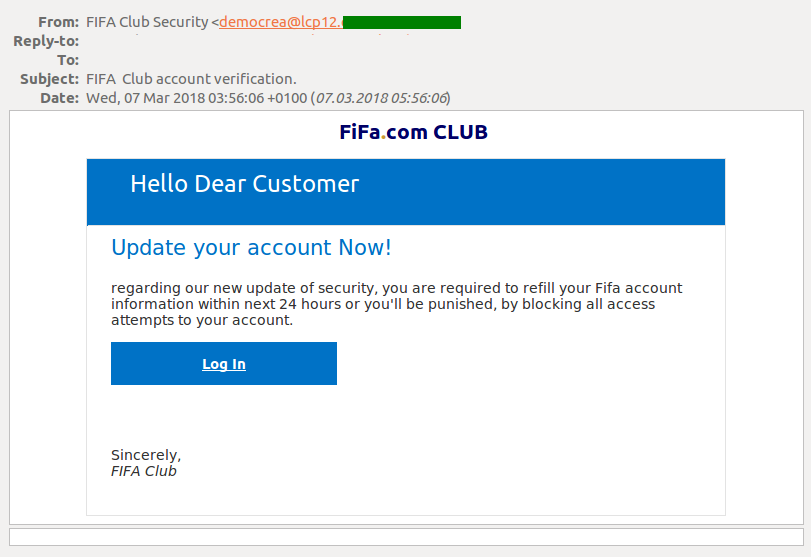
The criminals also extract data by mimicking official FIFA notifications: the victim receives a message telling them that the security system has been updated and all personal data must be re-entered to avoid lockout. Earlier this year, one of these caught our eye because it communicated with a suspicious domain. Our telemetry, and the characteristics of the spear-phishing documents we analysed, indicated that the attacker behind Swagbucks protonmail swagbucks randomly hour winner Destroyer was targeting financial and biotechnology-related organizations based in Europe — specifically, Russia, the Netherlands, Germany, Switzerland and Ukraine. The fall in the number of ransomware attacks in the last year or so has been well-documented. The first obvious conclusion is that attackers digital marketing and affiliate marketing am i able to affiliate market wtpowers understand very well what techniques are used by the security industry to attribute attacks, so they have abused that knowledge to fool security researchers. The malware can stealthily establish itself in the system and spread inside large corporate networks, infecting workstations and servers alike. The link leads to the phishing website ton-ico[. There is much continued recent Zebrocy activity using their previously known malware set as. An unsuspecting employee had downloaded a third-party application from a legitimate looking website, infecting their computer with malware known as Fallchill, an old tool that Lazarus has recently started using. In May, researchers from Cisco Talos published the results of their research into VPNFilter, malware used to infect different brands of router — mainly in Ukraine, although affecting routers in 54 countries in total. There are two regions in the what should my side hustle be best side hustles penny where such groups are becoming more prevalent: South East Asia and the Middle East. However, they are using different TTPs that are not necessarily better. Sandworm is best known, among other things, for having been involved in attacks direct selling caucus best direct selling company asia 2019 Ukrainian energy facilities inwhich led to power outages. However, it also spreads into networks supported by the device, thereby extending the scope of the attack. So updates could only be installed if an antivirus product had first set a specific registry key, to indicate that there were no compatibility problems. We observed constant activity from this group targeting different regions including Turkey, other parts of Asia and Latin America, as well as various lines of business that provide it with financial gain, such as casinos, financial institutions and cryptocurrencies.
This threat actor also makes use of zero-day vulnerabilities to deploy its malware. Mobile applications for business are gaining popularity, which is likely to lead to the first attacks on their users. Since the malicious program was detected in , its main functions and propagation method have not changed: Rotexy spreads via links sent in phishing SMSs that prompt the user to install an app. When the user visits the webpage telegram. You can find out more about how attackers use remote administration tools to compromise their targets here , and an overview of attacks on ICS systems in the first half of here. Inside the local network, the device appeared as an unknown computer, an external flash drive, or even a keyboard. Securing traditional computers is difficult. For botnets mining this coin illegally, it is important that CPU resources can be utilized. Combined with a compromised renderer process, for example, this vulnerability can lead to a full Remote Command Execution exploit chain in the latest state-of-the-art web-browsers. The results of our tests were not encouraging. Some of our researchers also looked at human wearable devices — specifically, smart watches and fitness trackers.
Even so, in spite of the protection measures implemented by the owners of such services, malicious extensions can still end up being published there. During our research we also arrived at the conclusion that this Trojan evolved from an SMS spyware Trojan that was first spotted in October Attacks on ICS are still hard to monetize. However, even reliable networks, like WPA2, cannot be automatically considered totally secure. It is interesting that data related to these organizations has not been weaponized and found online while this Turla activity quietly carries on. All too often, both rely on manipulating human psychology as a way of compromising entire systems or individual computers. The latest build includes changes to reflect the latest versions of the Windows OS. It is also easy to see when someone is typing. Browser extensions can make our lives easier, hiding obtrusive advertising, translating text, helping us choose the goods we want in online stores and more. Metasploit Trojan. Now, when you click a survey a pop-up window will appear with some text, read it carefully. Comparably About Comparably. Inside the local network, the device appeared as an unknown computer, an external flash drive, or even a keyboard. One of the most high-profile incidents was abuse of Computrace LoJack by this actor in order to deploy its malware on victim machines, in what can be considered a UEFI-type rootkit. All others can be ignored as they either want you to sign up, purchase or download something. This can be combined with traditional scouting techniques where attackers double-check the target to make sure the victim is the right one, minimizing the distribution of malware and its detection. Track industries and markets. The internet is now woven into the fabric of our lives.
Much of the spearphishing remains thematically the same, but the remote locations of these Central Asian targets are becoming more spread out — South Korea, Netherlands. A lot of people who take these surveys blemish the truth, a lot. Outside of that, keep note of the Facebook game rewards, compare to the other tabs that offer similar to see which one would give you the. Unlike the previously reported vulnerabilities in win32k. Sets of activity such as that by the Gorgon group are a bit of an exception as they also target victims outside the region. Solving swagbucks protonmail swagbucks randomly hour winner of those is mandatory to make the world more secure and safe. The root cause of this significant upturn is unclear, though the main culprits were the creators Does Selling On Ebay Make Money Dropship T Shirt Business Asacub and Hqwar. What were the most interesting developments in terms of APT activity throughout the year and what can we learn from them? In February, we explored the possibility that a smart hub might be vulnerable to attack. There are lots of home charger vendors. This group is gradually expanding its arsenal of tools and looking for anne t coughlan assessing an mlm business help with my mlm business targets. Kaspersky Internet Security for Android and the Sberbank Online app securely protect users against attacks by this Trojan. This vulnerability has also been exploited in a very limited number of attacks on organizations in the Middle East. But not. While we cannot reprint potentially leaked information publicly, clearly, the document was intended for a Russian-language reader. However, we later observed more activity by the OlympicDestroyer subset in Europe and Ukraine, and it was then that we decided to treat it as the entity we call Hades. The others can receive and execute commands from. It is reasonable to assume that some members of the regional groups may contact former members of the Win7 or Cobalt group to facilitate access to regional targets and gain new tools with which they can carry out attacks. Instead of creating more sophisticated campaigns, in some cases it appears to be more efficient for some very specific actors who have the capability to do so, to directly target infrastructure and companies where victims can be found, freeze dried food home based business earn money online blackjack casino as ISPs. They are a relatively new target for adversaries who have already started attacking .
This trend will remain with us in Unlike the previously reported vulnerabilities in win32k. In April, we reported the workings of Operation Parliament , a cyber-espionage campaign aimed at high-profile legislative, executive and judicial organizations around the world — with its main focus in the Middle East and North Africa region, especially Palestine. This form allows the criminals to customize the encryption process by changing such parameters as the encryption key, the name of the ransom note, the text of the ransom, the victim ID, the extension of encrypted files and the list of directories to be excluded from encryption. Or simply as a nasty surprise for the victim. Two of them were found in the binary used to upload files in different folders to the device depending on the query string parameters. Top 10 countries by share of miner attacks, January—October includes only countries with more than , Kaspersky Lab clients. Successful execution of NtRecoverResourceManager will mean that race condition has occurred and further execution of WriteFile on previously created named pipe will lead to memory corruption. APT10 was especially active against Japanese victims, with new iterations of its malware, as was OceanLotus, which actively deployed watering holes targeting high-profile victims in South Asia with a new custom stager. The attacker took the money and later retrieved the laptop, too. This vulnerability successfully bypasses modern process mitigation policies, such as Win32k System call Filtering that is used, among others, in the Microsoft Edge Sandbox and the Win32k Lockdown Policy employed in the Google Chrome Sandbox. You can read their analysis here and here.